The Access-Risk Landscape in 2022
Blog Article Published: 07/06/2022
 Written by Marie Prokopets, Co-founder and COO, Nira.
Written by Marie Prokopets, Co-founder and COO, Nira.
Introduction
The number of data breaches and cases of unauthorized access to cloud-based documents, what we call — Access-Risk incidents — has skyrocketed over the past few years.
In fact, 68% of information security professionals felt their organization is “extremely to moderately vulnerable” to Access-Risk incidents, with the same percentage reporting these data breaches are becoming more frequent, according to Cybersecurity Insiders.
Access-Risk is also becoming more expensive: in 2020, it cost an average of $645,000 to clean up these incidents, according to the Ponemon Institute.
Survey after survey has demonstrated that well-intentioned employees are the number one cause of unauthorized data and document access. The underlying reasons — negligence, mistakes, overlooked details — are a result of human nature.
We argue a solution will be based on a supportive and holistic approach that educates and enlists employees in proper Access-Risk practices.
In this article, we’ll explore:
- The urgent problem of Access-Risk for every size organization
- Business implications to be aware of
- How to implement a holistic approach to managing Access-Risk in your organization
For a closer look at the research, download the full Access-Risk Landscape in 2022 report.
What is Access-Risk mitigation?
It's more critical than ever for organizations to protect their sensitive information. With the spread of collaboration tools and their usage, data has never moved with greater ease, causing a record number of exposure points.
Data is increasingly shared with third parties: partners, customers, vendors, freelancers, and contractors, meaning the old dichotomy of internal versus external threats is increasingly outdated.
Responsibility for securing these data assets often falls on employees who may lack training and tools, or who are overburdened by the stresses of high growth or pressure brought on by the pandemic and multiple global crises.
While unnerving for IT professionals, collaboration and a free flow of data are the norm in today’s workspaces and must be accommodated in a secure manner.
Access-Risk mitigation is an approach to data security that aligns an organization’s data-access policies with the realities of today’s highly-collaborative and distributed workplace. Let’s examine the growing problem of Access-Risks and the impact they have on business needs.
Access-Risk stats and business impact
The average number of Accident-Risk incidents per organization grew at an alarming rate, from 14.5 in 2016 to 23.1 in 2020, a stunning 59 percent increase, according to the Ponemon Institute.
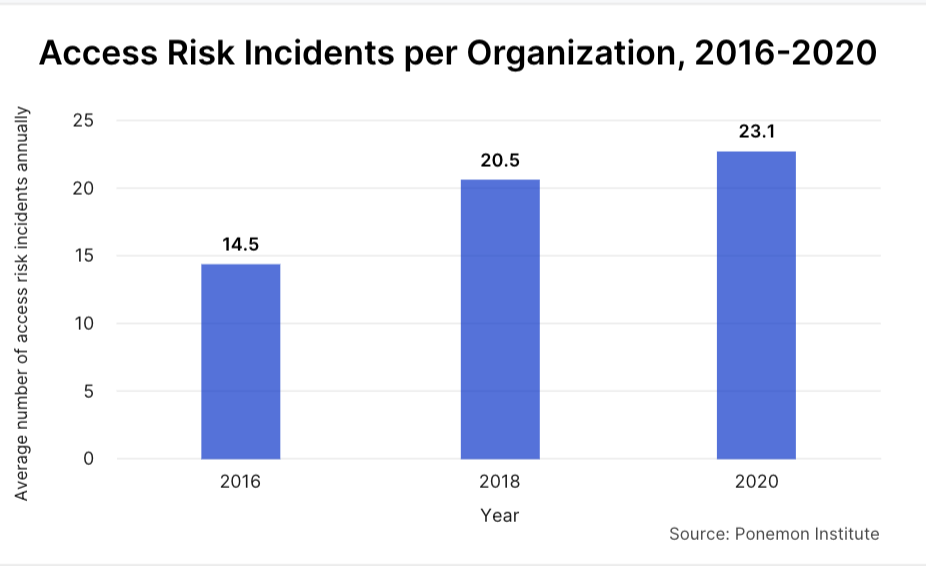
The most harmful impact for companies is often reputational: leaks to media may result in erosion of stock price or damage to the brand.
They also encompass the theft of trade secrets leading to costly litigation or the revelation of code that’s central to the operating model of the company.
There’s also the compromise of customers' personal information that destroys trust and may lead to expensive public admissions and cleanups.
These incidents also take a toll on IT and security teams, who can spend months of their time investigating breaches, patching vulnerabilities, and dealing with compliance repercussions.
Companies who hold sensitive customer data like protected healthcare information, financial assets, or creative or customer IP, should be especially wary of allowing this data to fall into the wrong hands.
What causes Access-Risk incidents?
Ponemon Institute found the vast majority of Access-Risk incidents are not malicious. In fact, nearly 80 percent of Access-Risk incidents are the result of human error. Rather than shadowy hackers or disgruntled employees, Access-Risk incidents happen mainly due to negligence.
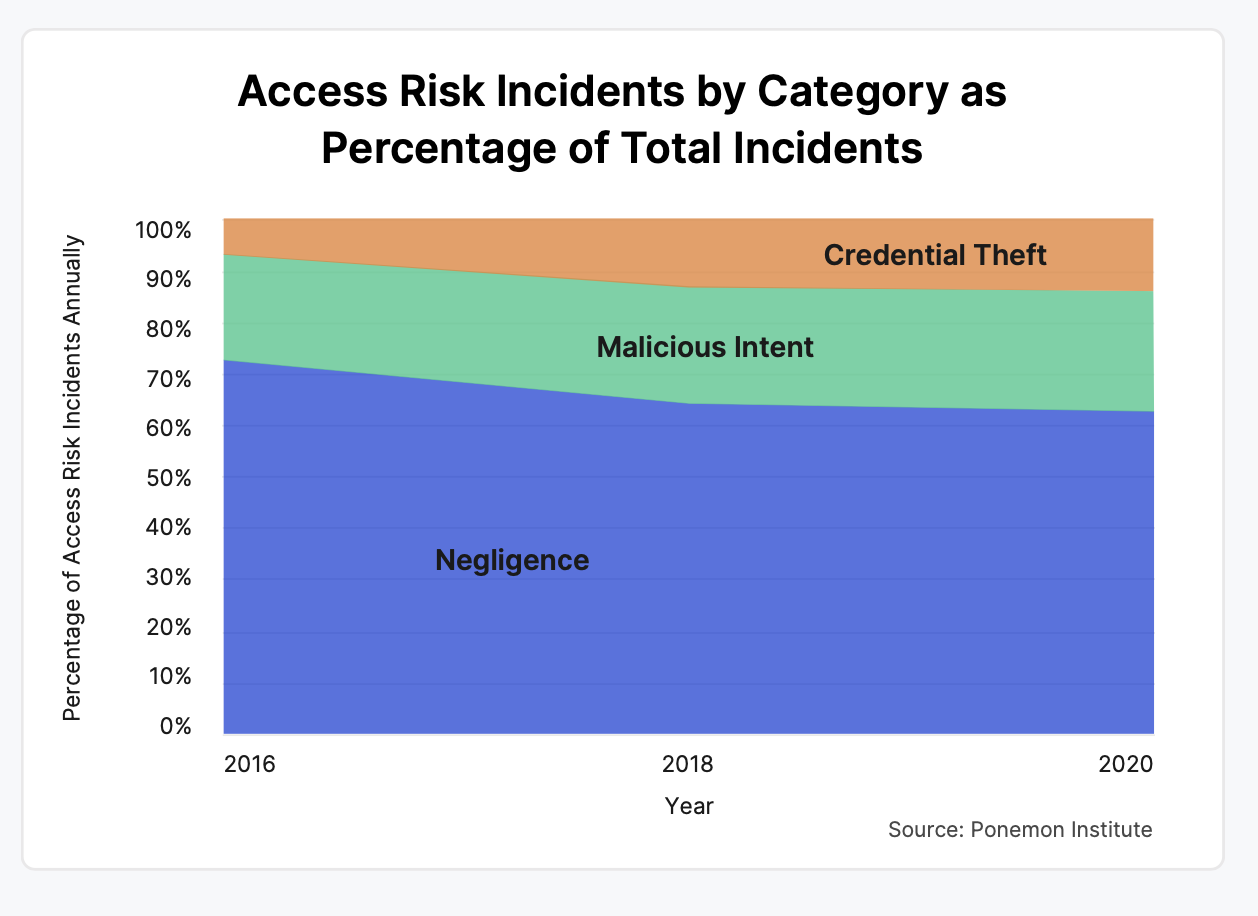
While this may seem like a silver lining, even benign intentions can have a detrimental effect on an organization’s finances. The costs to your organization are ultimately agnostic on the origins of an Access-Risk event and can result in massive damage to the company.
Access-Risk programs must acknowledge the realities of employee behavior and human error.
An Access-Risk approach seeks to work with employees, to facilitate their workflows instead of hindering them. With the proper tools and education, employees are often your best asset.
Cloud security tools and training help companies and empower employees
A majority of employees consider themselves part of the front line when protecting access. For example, a survey by Nira found nearly 55% of employees believe that they are responsible for securing access to company documents. However, many organizations don’t invest in the right tools or education to aid their end-users.
.png)
Employees need proper training and visibility to keep documents secure and protect company data from unauthorized access. To help, we created an in-depth ebook on document security for companies using Google Workspace, as well as an Employee Portal for delegating Access-Risk remediation to employees.
We recommend that employers—in companies of all sizes—openly communicate to employees about Access-Risk questions and explain why every employee has a stake in securing company information.
Where does Access-Risk go from here?
Companies need proactive insight into Access-Risk issues before they become Access-Risk incidents. We expect in coming years this will be augmented by a growing integration of AI and machine learning capabilities into data security solutions, providing automated, real-time reporting on potential issues.
An Access-Risk approach will require internal expertise—from departments like compliance and legal—and the help of employees and managers to enable solutions. Security policies should be perfected over years, not thrown together in the wake of a debilitating incident that may lead to damaging overcompensation.
Technology alone, we believe, will never completely solve the problem of Access-Risk. A technological solution to Access-Risk will only be as effective as the organizational culture that utilizes it.
For how to implement an Access-Risk approach in your organization, read the full report.
 About the Author
About the Author
Marie Prokopets is the Co-founder and COO of Nira, a
real-time access control system designed to protect cloud-based company
information from unauthorized access. She previously worked at Diageo, where
she focused on innovation, M&A, and strategy. She also spent time at PwC
working with Fortune 500 companies and private equity firms on their corporate
strategy and acquisitions.
Trending This Week
#1 The 5 SOC 2 Trust Services Criteria Explained
#2 What You Need to Know About the Daixin Team Ransomware Group
#3 Mitigating Security Risks in Retrieval Augmented Generation (RAG) LLM Applications
#4 Cybersecurity 101: 10 Types of Cyber Attacks to Know
#5 Detecting and Mitigating NTLM Relay Attacks Targeting Microsoft Domain Controllers
Related Articles:
Why Business Risk Should be Your Guiding North Star for Remediation
Published: 04/25/2024
Upselling Cybersecurity: Why Baseline Security Features Shouldn’t Be a Commodity
Published: 04/24/2024
Secure Your Kubernetes Environment by Enforcing Least Privilege
Published: 04/24/2024






