What is Gartner’s SASE Model, and How Will it Affect Your Cloud Security Stack?
Blog Article Published: 11/09/2021
 By Chloe Whitaker
By Chloe Whitaker
Originally Published by Cisco on August 31, 2021
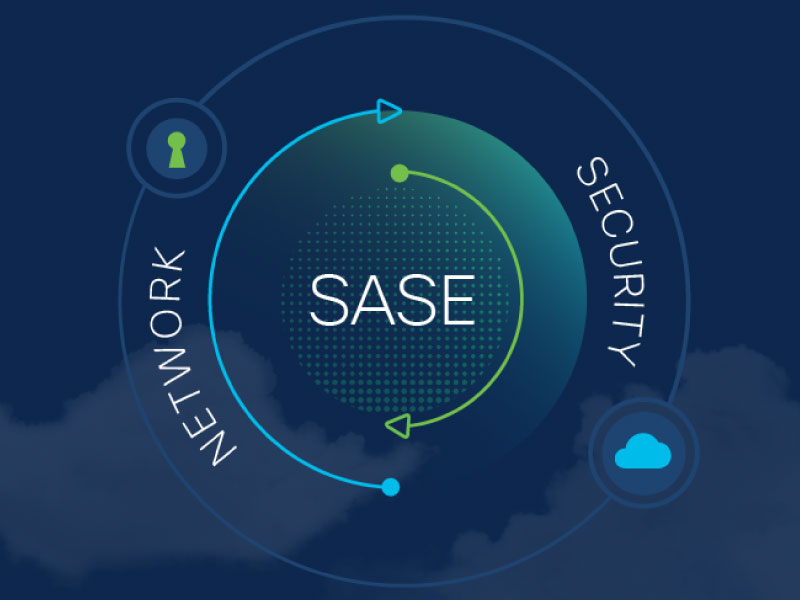
The way we think about networking and cybersecurity has changed dramatically in recent years. The rise of remote workers, coupled with the growing push of company data and infrastructure into the cloud, prompted Gartner to outline a new approach to networking and security: Secure Access Service Edge (SASE). Where an organization’s networking and security solutions were once siloed, Gartner’s SASE model converges this critical infrastructure into a single, cloud-delivered service.
The benefits of a SASE solution – its rapid time to value, its streamlined deployment and management, its cloud-native architecture – speak for themselves. Oftentimes, though, organizations lack the resources to jump straight into upgrading their entire infrastructure. What’s more, today’s SASE vendors may lack the resources necessary to offer a truly integrated solution. While some vendors can provide an integrated networking and security architecture, others will offer a SASE solution that integrates their own offerings with that of other vendors. For businesses owners and security teams, this usually means that upgrading to Gartner’s SASE framework happens in stages: a security refresh that will eventually lead to a network upgrade or a network refresh that integrates security solutions over time.
While there’s much to be said about the benefits of configuring your network with SASE in mind, today we’ll be focusing on the security elements of a SASE solution. Starting your journey towards SASE by converging your siloed security solutions into a single, cloud-delivered stack can streamline deployment and management for your security team while also enhancing cybersecurity for any remote employees or digital nomads working at your company.
If you’d like to learn more about what is included in a SASE security stack – and how one of these solutions works – we’ve put together this helpful guide.
The Modern Cybersecurity Landscape
We’ve come a long way since the first ransomware attack crippled a network after being distributed via hand-delivered floppy disks. These days, your network probably isn’t even located in a single place – Gartner forecasts that 51% of global knowledge workers will be full-time remote by the end of 2021.1 And this prediction only factors in full-time remote workers – Forbes reports that 97% of employees would prefer some flexibility when dividing their time between an office building and their home office.2
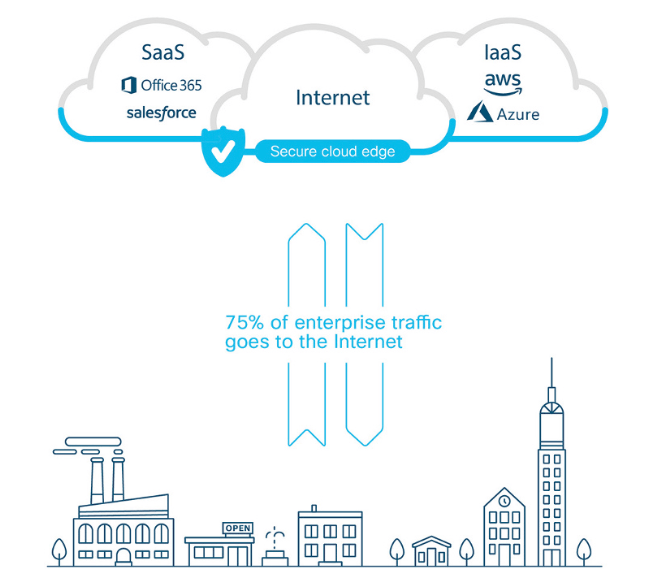
This shift in employee location is enabled by the growing popularity of SaaS, PaaS, and IaaS solutions amongst business leaders. However, while this push to the cloud may streamline business processes, it also leaves sensitive data and company networks vulnerable to bad actors. In fact, security teams often find themselves managing many cybersecurity solutions to protect company data stored with third-party providers and accessed over the Internet.
This isn’t easy on SecOps teams. In fact, a 2020 Cisco CISO Benchmark study3 recently revealed that 16% of enterprise security teams field more than 100,000 alerts on a daily basis! With functionality like this, it’s no wonder that many SecOps teams find themselves facing:
- Gaps in visibility and coverage, leading to inevitable breaches
- Slow deployment times, as updating or upgrading multiple cybersecurity solutions requires coordination
- Limited budgets and resources, since multiple cybersecurity tools require multiple subscriptions
Fortunately for today’s frantic SecOps teams, Gartner’s SASE model presents a solution to these security challenges.
What Is the SASE Difference?
Think of your cybersecurity stack like a group project – great in theory, but capable of quickly turning into an exercise in frustration. Some of the group members contribute more than others, everyone experiences communication troubles, work gets doubled up on – or forgotten entirely – and no one is entirely sure what they’re supposed to be focusing on. This is the picture of a siloed security stack.
Siloed security stacks are labor intensive, because moving threat data between multiple security solutions is either difficult or impossible. Your security team must create policies in multiple systems, some of which are more useful than others. These solutions also generate a barrage of notifications, making it difficult to identify real threats. And at the end of the day, most of the effort is focused on securing company data centers as opposed to securing the cloud, even though employees spend more time in the cloud on a daily basis.
Compare this to what a group project should be: a coordinated team where every member performs a unique task, sharing the results with other team members to create a focused, optimized, and functional project. This is a security stack built on Gartner’s SASE model.
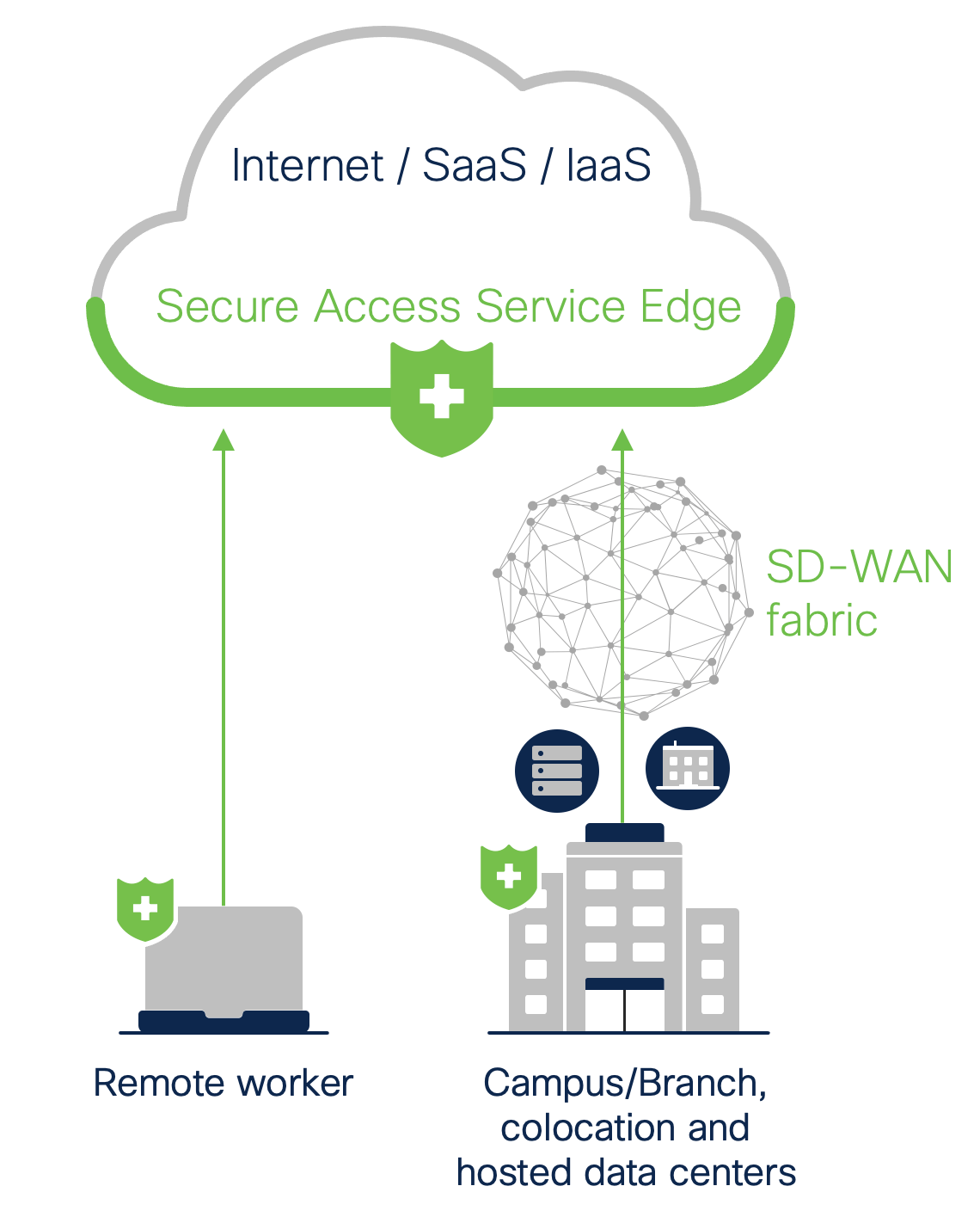
Gartner defines the SASE concept as “an emerging offering combining [wide-area network] capabilities with comprehensive network security functions…to support the dynamic secure access needs of digital enterprises.”4 In a SASE solution, every element of your security stack comes from the same provider and is designed to fill a specific need. The different security solutions also function together seamlessly. For example, data provided by a robust threat intelligence network can inform a secure web gateway (SWG) to block web activity associated with files hosted on a known malicious domain. If the nature of the files can’t be identified, the SWG can send them to the cloud sandbox to determine their capabilities and block future attempts to connect to the domain if necessary.
Best of all, a security stack built for a SASE solution allows teams to manage all these functionalities through a single, easy-to-navigate interface. Here, security teams can create and implement policies designed to provide protection at the cloud edge, where most user activities occur. All SASE security functionality is both identity-centric and cloud-native, with security measures focusing on the identity of the user or device instead of on the data center. A zero-trust network access (ZTNA) solution plays an important role here, as it helps determine whether a user should have access to data and applications.
So, how does one evaluate whether a cybersecurity solution has all the components necessary as part of a SASE system?
Understanding the Security Parts of a SASE Solution
A true SASE system ought to include several different types of threat protection. At minimum, a SASE security stack should include:
- Secure web gateway (SWG)
- Cloud access security broker (CASB)
- Data loss prevention (DLP)
- Cloud-delivered firewall (FaaS)
- Zero-trust network access (ZTNA)
For maximum protection and control, however, your SASE security stack should also include:
- DNS-layer security
- Remote browser isolation (RBI)
- Detection for malware in cloud storage
- Interactive threat intelligence
As mentioned above, all these security solutions should integrate seamlessly with SD-WAN functionality that comes from the same provider. Additionally, a security team should find it simple to the manage entire system from an easy-to-manipulate and easy-to-understand interface.
This fluid convergence of cybersecurity and networking is what makes Gartner’s SASE security model shine. Ultimately, it’s also what helps many CISOs and security teams go from asking, “What is SASE?” to asking, “How can I get a SASE system for my network?”
1 Gartner, Gartner Forecasts 51% of Global Knowledge Workers Will Be Remote by the End of 2021. Laurence Goasduff, 22 June 2021.
2 Forbes, 5 Statistics Employers Need to Know About The Remote Workforce. Ashira Prossack, 10 February 2021.
3 Cisco, Cisco 2020 CISO Benchmark Report. 2020.
4 Gartner, The Future of Network Security Is in the Cloud. 2019.
Trending This Week
#1 The 5 SOC 2 Trust Services Criteria Explained
#2 What You Need to Know About the Daixin Team Ransomware Group
#3 Mitigating Security Risks in Retrieval Augmented Generation (RAG) LLM Applications
#4 Cybersecurity 101: 10 Types of Cyber Attacks to Know
#5 Detecting and Mitigating NTLM Relay Attacks Targeting Microsoft Domain Controllers
Related Articles:
How to Prepare Your Workforce to Secure Your Cloud Infrastructure with Zero Trust
Published: 04/24/2024
What’s in a Name? Defining Zero Trust for Leaders
Published: 04/22/2024
Implementing a Data-Centric Approach to Security
Published: 04/19/2024
7 Common Causes of Data Breach: Safeguarding Your Digital Assets
Published: 04/18/2024






