2022 Threat Report: Cloud-Native Threats are Increasing and Maturing
Published 11/04/2022
Originally published by Sysdig.
Written by Michael Clark. Sysdig.
The first annual cloud-native threat report from Sysdig explores some of the year’s most important security topics in the cloud. As the use of containers and cloud services keeps growing, threat actors are increasingly turning their attention to this new attack surface. The cloud offers unique opportunities for threat actors due to the inherent scalability and complexity of cloud resources.
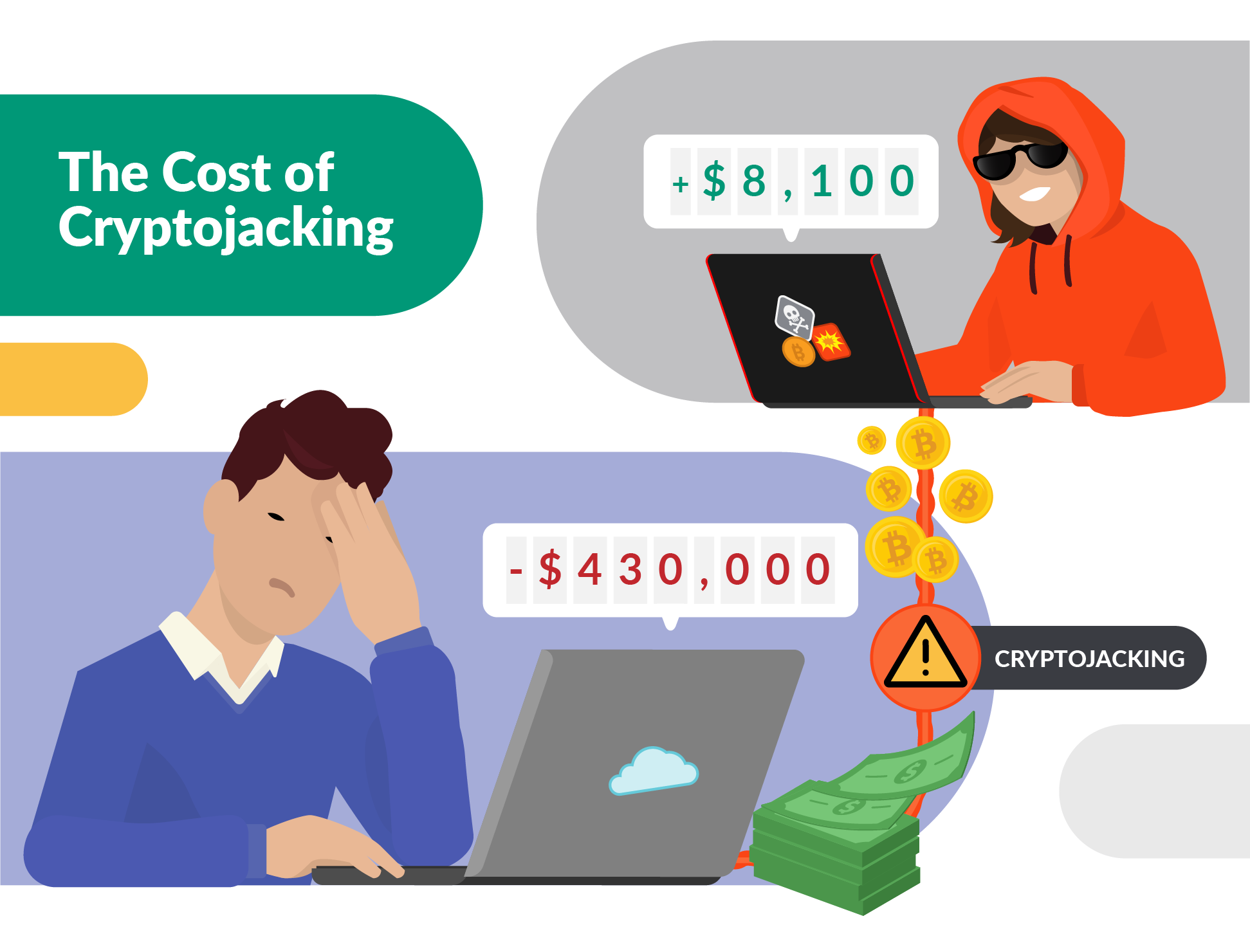
It turns out, a single malicious person can be prolific and quite impactful just by abusing misconfigurations and old exploits. As we will see, they can earn thousands of dollars almost passively off of their victims’ infrastructure.
Containers are great, as they allow developers to quickly get infrastructure up and running. However, threat actors can hide malicious code inside of these pre-built containers. If one wrong image is loaded, the entire environment can be compromised.
It is easy to think threat actors are all about profit or espionage. The Russian invasion of Ukraine shows that geopolitical events can prompt a shift from profit making to participating in conflicts through cyber attacks.
Let’s take a look at some highlights. Download the full report for more.
The real costs of cryptomining
Cryptomining continues to increase in popularity among profit-motivated threat actors. It has several advantages, such as having a much lower overhead than ransomware. The miner just needs to run on a computing resource, and the money starts coming in. There are also several privacy focused crypto coins that make it harder to get caught.
TeamTNT is the most famous of these cryptomining threat actors. It has operated for years and made at least $8,100 in directly attributed cryptowallets. This threat actor is likely just a single person and compromises targets of opportunity with scripted attacks, leveraging misconfigurations and unpatched vulnerabilities.
While cryptomining on its face may not seem like a serious threat, that all changes when the cloud provider bill comes due. The economics of cryptomining in the cloud can be severe for the victim. In order to generate $1 of profit for an attacker, it costs the victim $53!
The costs of a cryptomining breach can become massive over time or with a large enough scale.
Supply chain attacks from Docker Hub
According to the 2022 Sysdig Cloud-Native Security and Usage Report, 61% of all images pulled come from public repositories. Threat actors know this too, so they use these public repositories as an attack vector.
Sysdig Threat Research Team (Sysdig TRT) built a custom system to scan Docker Hub and identify malicious container images using both static and runtime analysis.
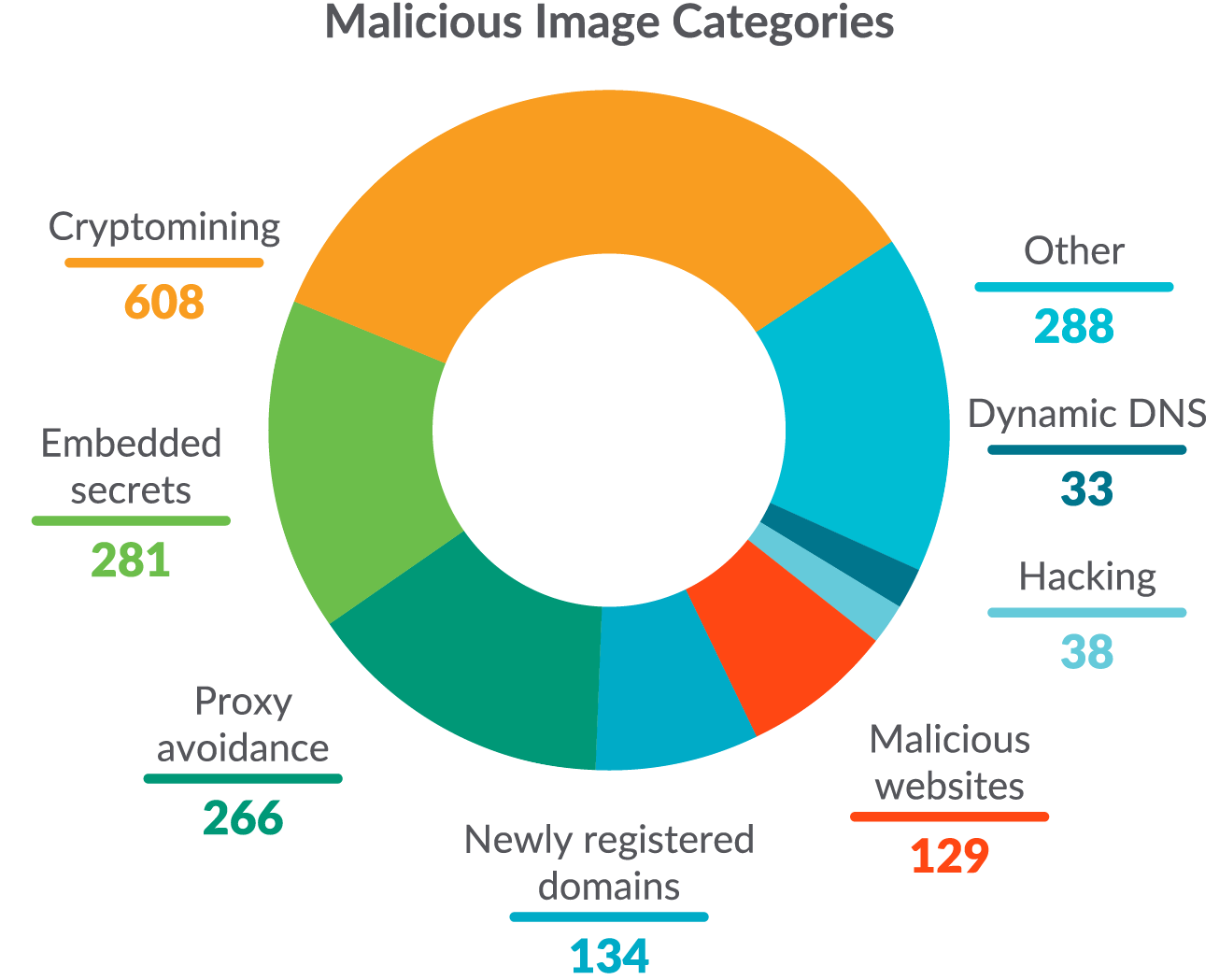
Over 250,000 images were scanned during the analysis, and the results showed that threat actors were actively using Docker Hub to spread malware. This mostly came in the form of cryptominers, which shouldn’t be a surprise at this point. However, malicious websites, hacking tools, and other unwanted software was also found in these images. Not only that, but embedded secrets were the second most common finding. Malicious containers were seen disguised as other legitimate packages, such as pytorch and Drupal.
It is critical that container users in an organization don’t use these malicious images by accident, as that could lead towards a much larger compromise through a supply chain attack. As a result, the Sysdig TRT created a continually updated feed of known bad container images, using their SHA-256 hashes in order to protect its customers.
Geopolitics and hacktivism
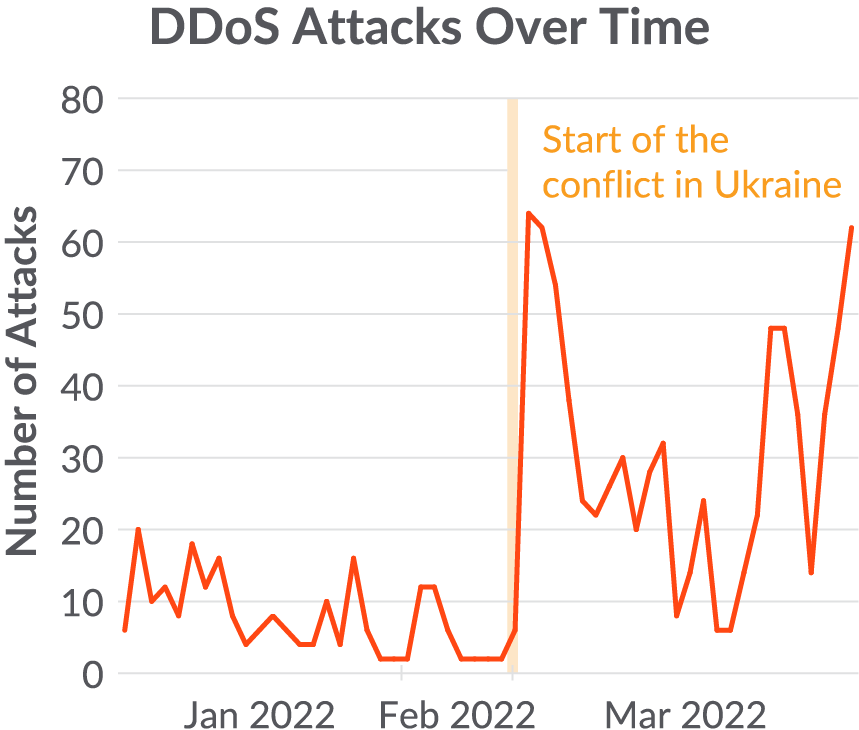
On Feb. 24, 2022, Russia began its invasion of Ukraine. Parallel to the military campaign, a cyberwar also began between the two sides. This is the first time cyberwarfare operations have been used in military operations in such a public way. More than 150,000 volunteers joined the Ukrainian side of this cyberconflict as hacktivists.
Distributed denial of service (DDoS) and destructive attacks using hard drive wipers have been the hallmark of the cyberwar, at least on the public facing side. Hacktivists from both sides have largely participated by joining the DDoS attacks. Starting almost immediately after the invasion began, the Sysdig global honeynet began to see a new trend emerge, a sharp rise in the amount of DDoS malware being installed. Prior to this, the majority of malware being installed was related to cryptomining.
Participants in the conflict also made it simple to get involved by using containers. DDoS tools with configurations that allowed users to automatically pull down target lists were pre-installed and rapidly distributed in Docker containers. These containers were shared using public repositories like Docker Hub. This lowered the bar substantially for people to get involved and increased the amount of participation on both sides.
Conclusion
Attackers are starting to understand how valuable cloud resources can be, whether the purpose is cryptomining, data theft, or as attack platforms. This trend will not change as more companies move to cloud from on-prem. That logic extends to containers, which are becoming another dependency that needs to be considered when thinking about threats to the supply chain. While the geopolitical situation as a whole is beyond the scope of the report, these events will continue to involve cyber more and more as countries start to depend on the resources that have moved to cyberspace.
Security and DevOps teams need to understand the threats they are facing so they can ensure that proper defenses are implemented. Visibility into cloud and container environments is critical as threats start to make use of these resources. A proper incident response can also only occur if visibility is available.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Core Collapse
Published: 02/26/2026
Token Sprawl in the Age of AI
Published: 02/18/2026


.png)
.jpeg)


